From ransomware protection to active directory digital twin, find out about Tropico's features
From ransomware protection to active directory, find out about Tropico's features
How Tropico Works in 3 Steps
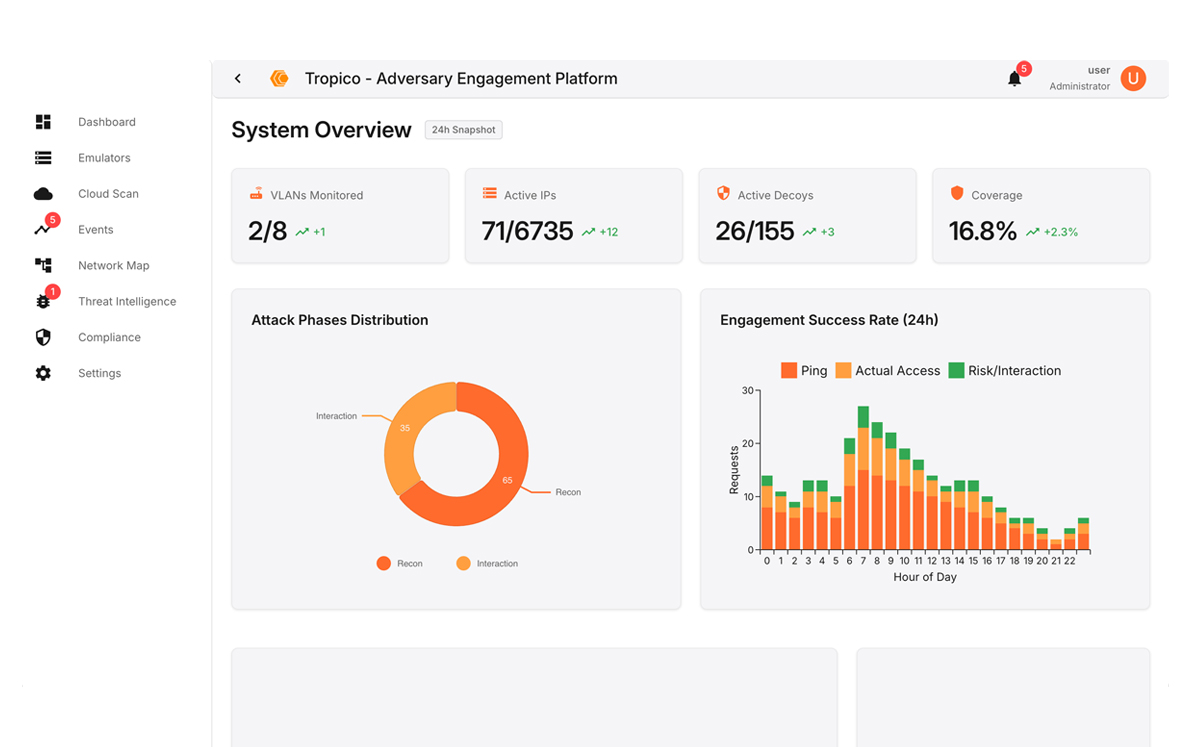

Collect Information
Tropico uses multi-layer intelligence: external and internal AI honeypot mazes, dark-web forums, SIEM alerts, and client threat intelligence to pull in any data related to attacks.

Deceive & Engage Adversaries
While attackers are busy in the AI honeypot mazes, our controlled environments that safely collect attacker behavior and tactics in real time, Tropico analyzes the attacker sessions and extracts data on the tactics and techniques used. This also increases the cost for the attacker and gives the SOC time to react.


Neutralize Before Damage is Done
Tropico immediately informs the SOC of any ongoing, imminent, and predicted attacks so that these can be blocked before damage is done. At the same time it automatically adds obstacles for attackers, for example stalling Ransomware attacks within the AI mazes.
Tropico AI Honeypot Maze
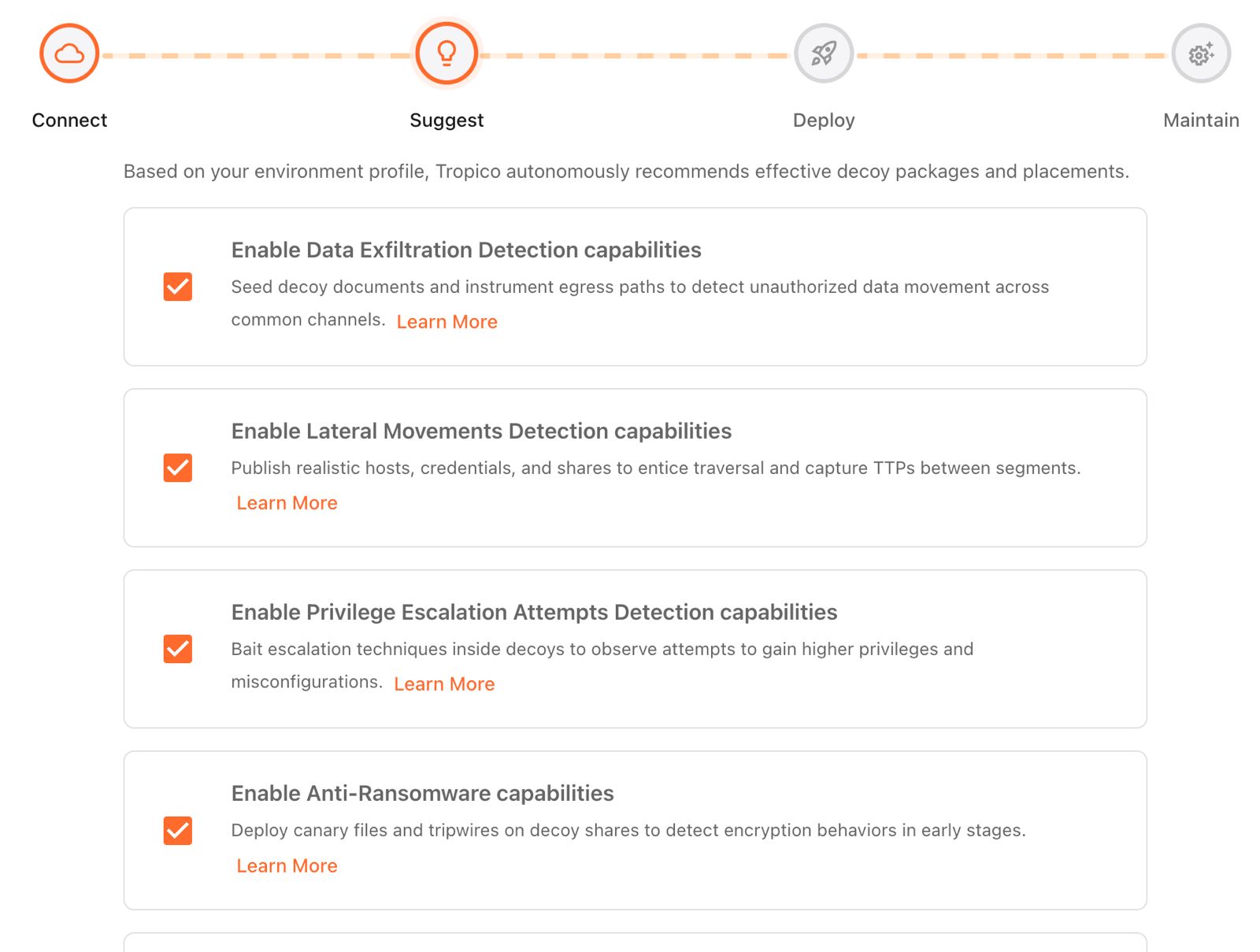
Connect
We profile your cloud environment using a secure read-only connection
Suggest
Autonomously recommends the best decoy package and where to deploy it
Deploy
It takes only a few minutes to get the decoys up and running in your infrastructure
Maintain
Decoys automatically adapt to changes in your infrastructure to remain realistic over time
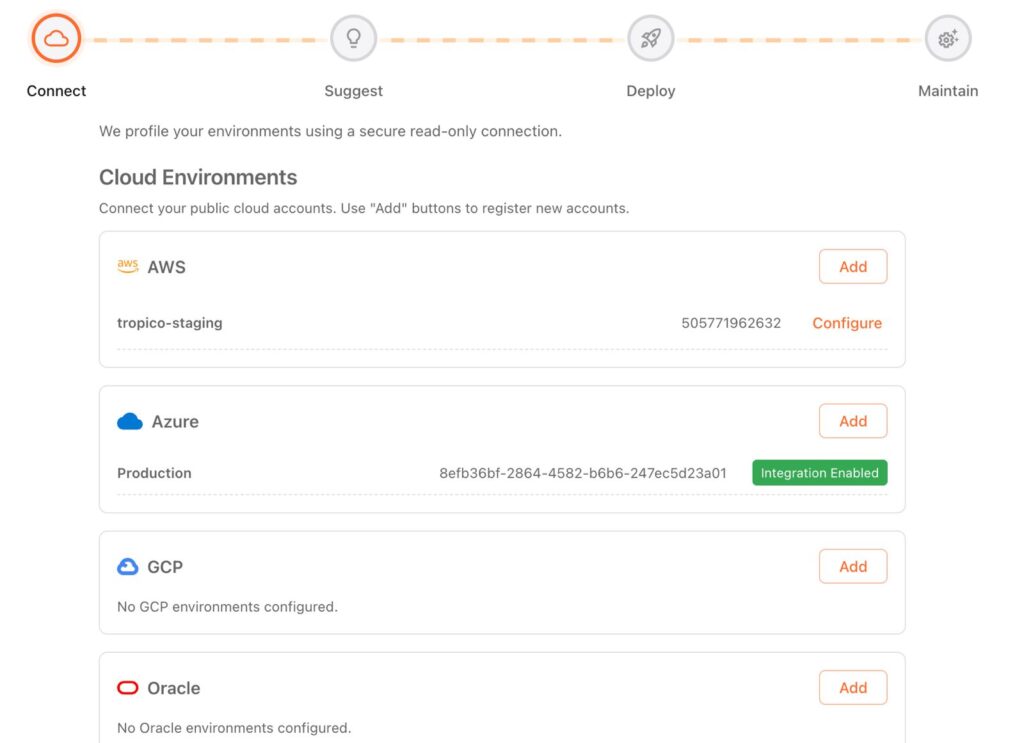
Connect
We profile your cloud environment using a secure read-only connection
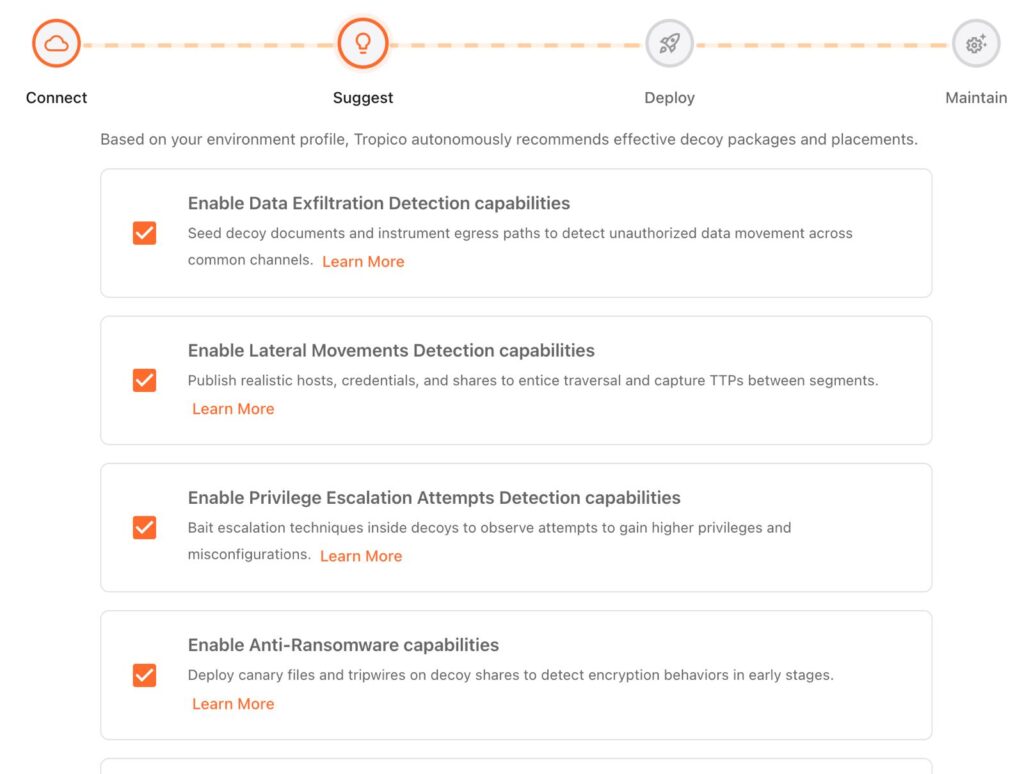
Suggest
Autonomously recommends the best decoy package and where to deploy it
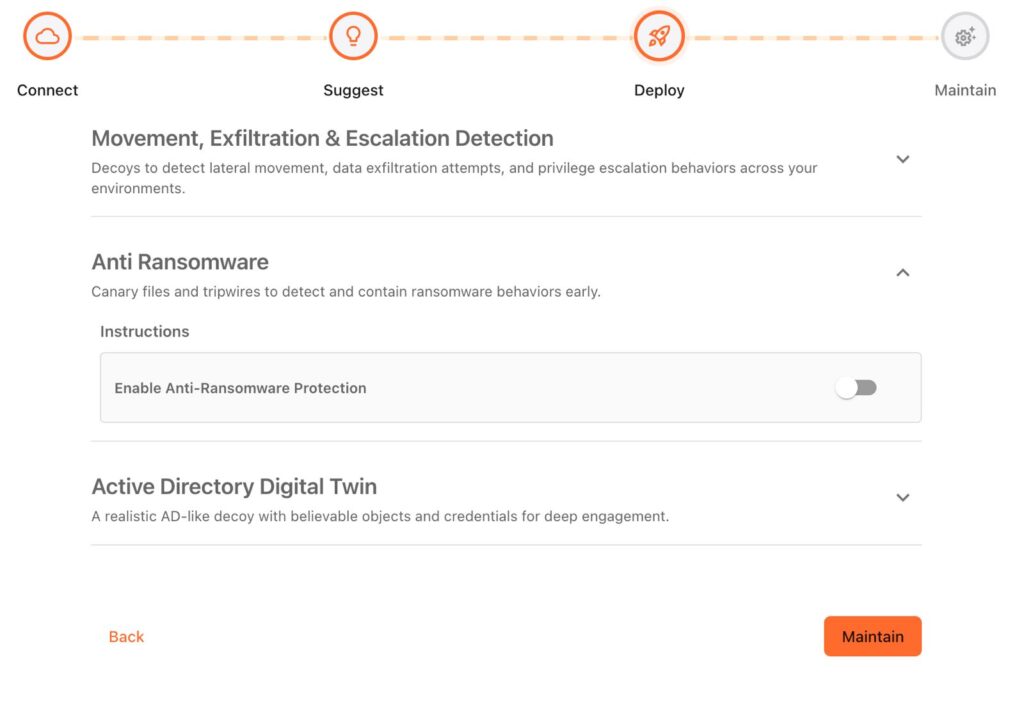
Deploy
It takes only a few minutes to get the decoys up and running in your infrastructure
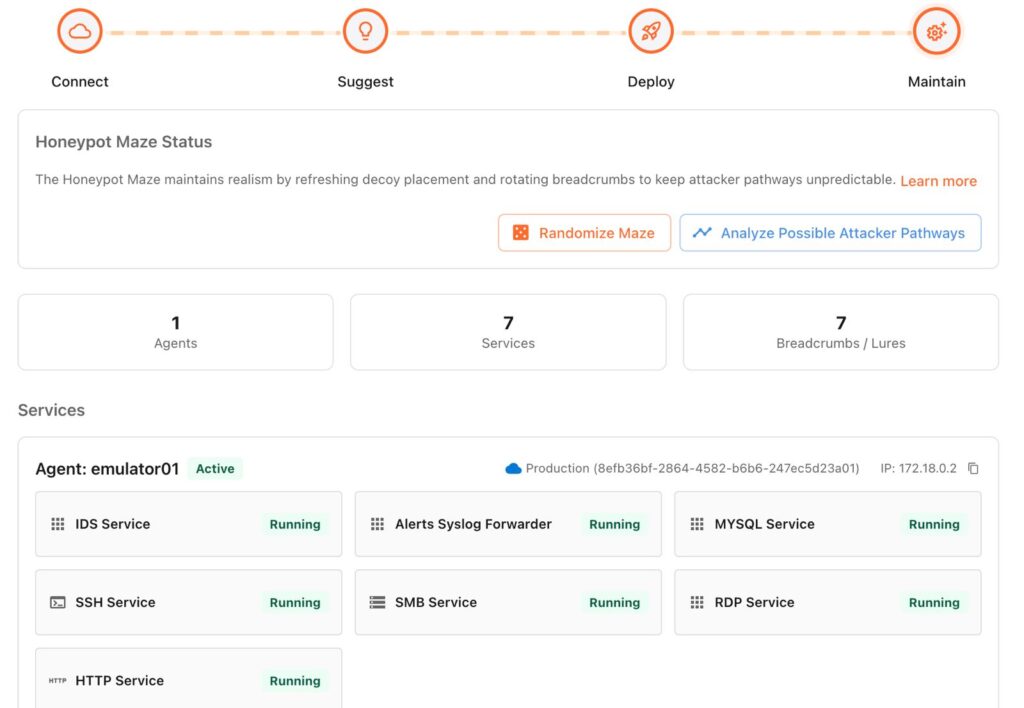
Maintain
Autonomously recommends the best decoy package and where to deploy it

