The Future of Cybersecurity is Preemptive.


Trusted by Experts working at





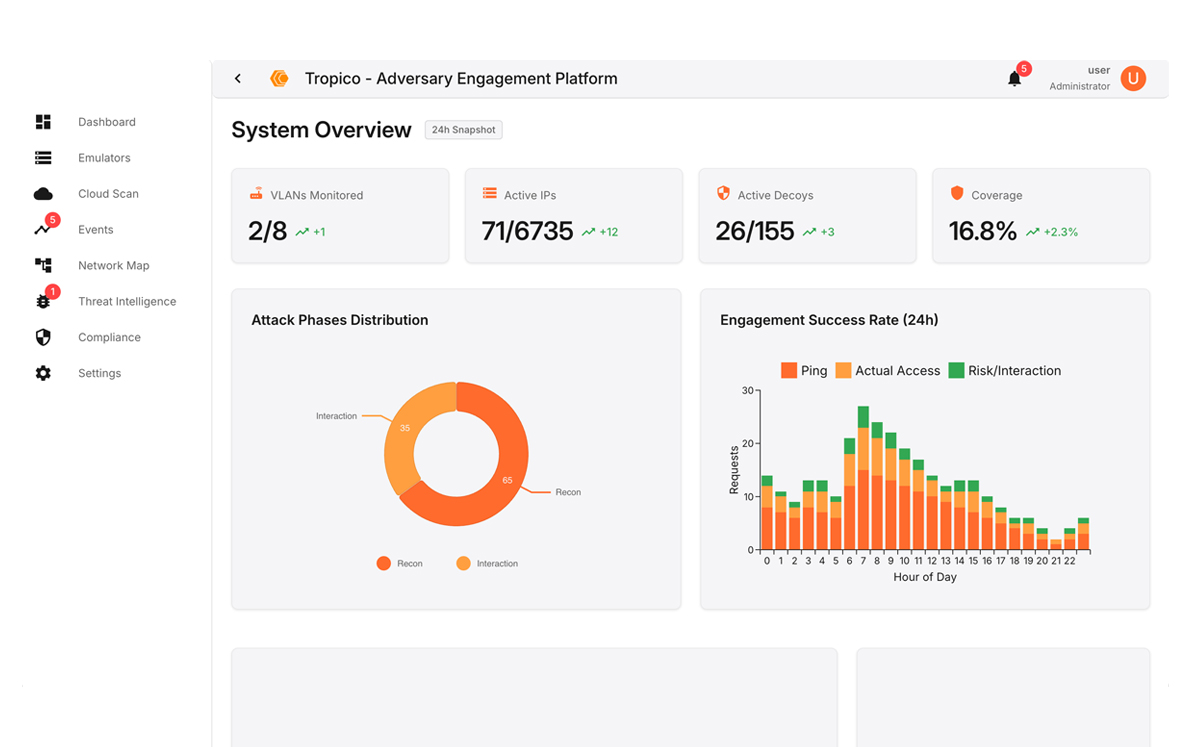
No surprises.Tropico predicts attacks and deceive adversaries.
Built to trap threats before they spreadWorried About?
Using SMB and RDP emulators, Tropico detects lateral movements of ransomware in real time. It also stalls ransomware in the encryption phase, buying the SOC precious time to respond.
Active Directory is one of the primary targets for attackers. By giving them a secondary active directory to scour through, they expose their tactics and we can alert the SOC in advance before the real deployments are compromised. Entra ID is also protected from phishing attacks.
Attackers take their time in a network after an asset is compromised. Sometimes it's hard to spot them for days, weeks, or even months. Recent attacks on critical infrastructure showed the attackers were within the network for over a year before going public. Tropico's emulators spot the attackers as soon as they try to move laterally within the network.
Compromised assets might not pose a threat until the attackers manage to escalate their privileges. Tropico gives attackers a playground to run their attacks harmlessly, within contained honeypots where the attacker behaviour is analyzed and their next moves are predicted and planned.
Ever wondered where the data that gets stolen from your enterprise ends up? Tropico gives attackers AI-generated information instead of real company data. This information is then tracked on dark-web forums to identify the attackers.
Using SMB and RDP emulators, Tropico detects lateral movements of ransomware in real time. It also stalls ransomware in the encryption phase, buying the SOC precious time to respond.
Active Directory is one of the primary targets for attackers. By giving them a secondary active directory to scour through, they expose their tactics and we can alert the SOC in advance before the real deployments are compromised. Entra ID is also protected from phishing attacks.
Attackers take their time in a network after an asset is compromised. Sometimes it's hard to spot them for days, weeks, or even months. Recent attacks on critical infrastructure showed the attackers were within the network for over a year before going public. Tropico's emulators spot the attackers as soon as they try to move laterally within the network.
Compromised assets might not pose a threat until the attackers manage to escalate their privileges. Tropico gives attackers a playground to run their attacks harmlessly, within contained honeypots where the attacker behaviour is analyzed and their next moves are predicted and planned.
Ever wondered where the data that gets stolen from your enterprise ends up? Tropico gives attackers AI-generated information instead of real company data. This information is then tracked on dark-web forums to identify the attackers.





